SSO (Single-Sign-On) in JISF (Part - 1)
What is Single-Sign-On (SSO)?
Single-Sign-On (SSO) is a mechanism to control access of users to a system, where a user logs in with a single username and password to gain access to a digital system(s). The major benefit of this mechanism is, the user does not need to remember or use multiple usernames and passwords.
When multiple digital services contain similar or correlated features, there comes a requirement of a Single-Sign-On facility, because otherwise for accessing each service there would require different usernames and passwords (therefore, credentials) which will become unmanageable. Moreover, accessing one service after another to do a task will become much troublesome. To solve this problem, Single-Sign-On is a wonderful mechanism.
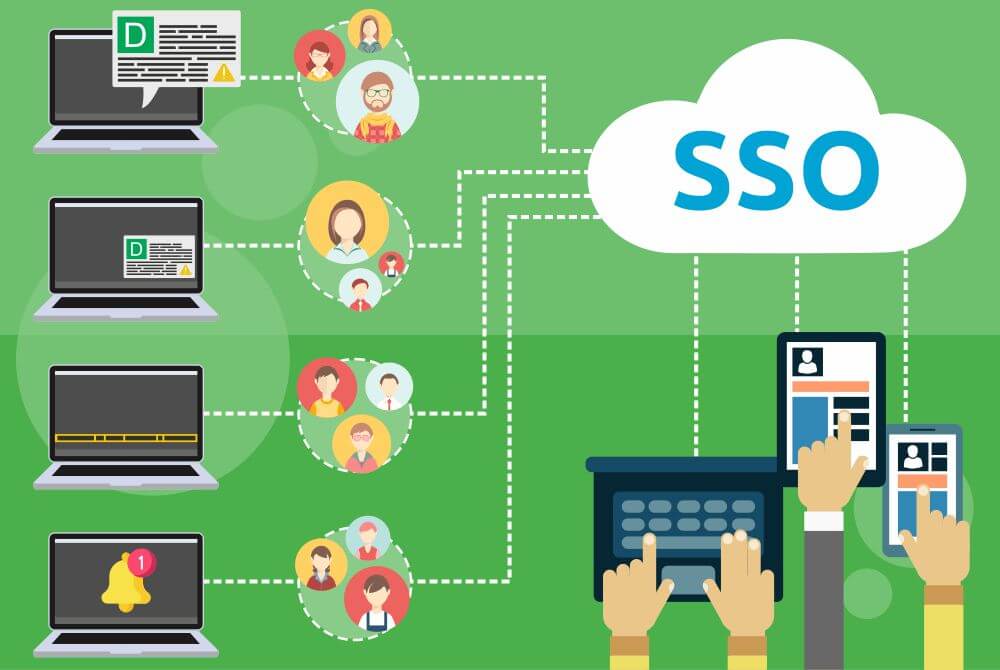
In this mechanism of Single-Sign-On, there remains an Identity Provider which contains a lookup facility that provides a mapping between network resources (in our case, different digital services), and this Identity Provider facilitates the same credential, and same access token to enter multiple services.
If even different digital services are of different types of authentication and login processes, the Single-Sign-On mechanism makes it very simple by facilitating a single-way login mechanism.
FIgure : SSO Integraiton
Why SSO is used in JISF?
JISF is such a platform with which all government judiciary digital services (known as, e-Judiciary) will be connected. As one governmente-Judiciary will have relation to another e-Judiciary, therefore a common access mechanism should be there while a Judge or Court Stuff accesses an e-Judiciary to facilitate citizen.
As an example scenario, if a Court staff wants to process a pending case file to any citizen, he will require to access the e-service service portal for the Court office. Here, to verify a case file with the applicant's NID the Court staff may require to access the e-service portal of Election Commission as well. In such a situation, if the staff of Court would get two different access credentials for wor e-service portals and if the officer would require to access them separately, then his task would become complex and time lengthy, For this reason, the JISF SSO Mechanism has made the life of Court staff easy by making a single login credentials and single authentication mechanism.
Benefits of using Single-Sign-On (SSO)?
There are so many benefits of SSO. The major benefits of SSO are:
- As SSO takes the responsibility of user authentication centrally, the services (that are going to use SSO) doesn’t require to think about implementing authentication
- The authentication and login management becomes centralized
- The user doesn’t require to remember multiple usernames and passwords for multiple services.
- The time to do activities on multiple services gets reduced as access to the services become so quicker using the same
- IT support expense reduces as calls regarding password change and recovery
- As it facilitates one URL, one Profile, one ID, one Password, therefore it removes the redundancy for the
For enterprise ecosystems where multiple digital services are centralized, and users of the ecosystem need to access each digital service quickly with a single credential, then SSO has no alternative.
How does SSO work?
There are different protocols (standard and of transmission) of Single-Sign-On. Among these, for JISF, the OpenID Connect (OIDC) is used on the top of OAuth2.0 Authorization Framework.
OpenID Connect (OIDC) is an authentication protocol that uses JSON Web Token (JWT), a type of token to validate and approve a login attempt.
And, OAuth 2.0 Authorization Framework uses this OIDC protocol and facilitates both authentication and authorization facility.
Here, Authentication is the process of verifying the identity of a user by obtaining some sort of credentials for example his username-password combination and using those credentials to verify the user’s identity.
When a user is authenticated using SSO to access any specific digital service, the “Identity Provider” of SSO issues an Access Token therefore an “Identity” to that the digital service can approve the user to access it.
Therefore, an Identity Provider offers user authentication as a service. An identity provider is a trusted provider that lets users use Single-Sign-On (SSO) to access software systems.
While implementing the SSO mechanism, Solution Architects use a type of Widget which helps users to switch among software systems that are connected with the SSO.
Widget, in general terms, is an independent web element that can be placed commonly on the user interface of any website or software to facilitate a set of features.
All the above-explained elements are part of the deployment of the SSO mechanism using OAuth
2.0. OAuth is not only a simple way to publish and interact with protected resource data, but it is also a safer and more secure way for people to give you access to their resource data. Organizations that have started to use OpenID Connect with OAuth 2.0 includes Amazon, Google, Facebook, IBM, Microsoft, Salesforce, VMWare etc.
Elements of SSO in JISF
OAuth 2.0 with OpenID Connect :-
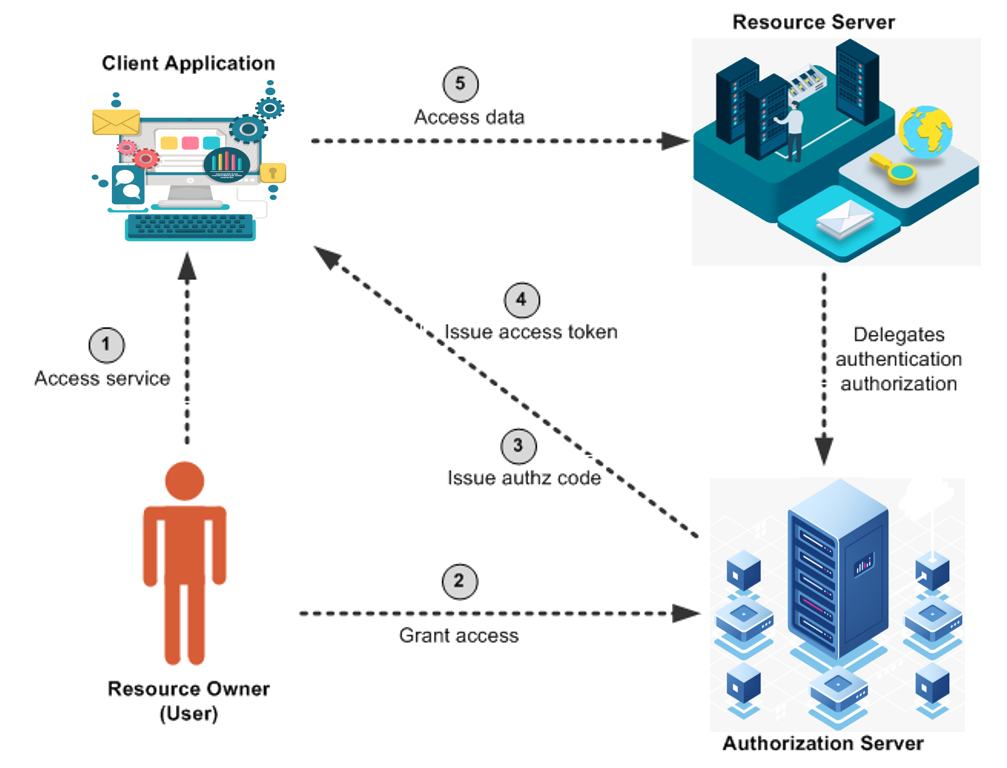
Roles of OAuth: OAuth defines four roles:
- Resource Owner
- Client
- Resource Server
- Authorization Server
We will detail each role in the following subsections.
Resource Owner: User
The resource owner is the user who authorizes an application to access their account. The application's access to the user's account is limited to the "scope" of the authorization granted (as an example, read or write access).
The resource server hosts the protected user accounts, and the authorization server verifies the identity of the user then issues access tokens to the application.
From an application developer's point of view, a service's API fulfills both the resource and authorization server roles. We will refer to both of these roles combined, as
the Service or API role.
Client: Application
The client is the application that wants to access the user's account. Before it may do so, it must be authorized by the user, and the authorization must be validated by the API.
FIgure: Client Applicaiton
Single-Sign-On Widget
In general terms, a Widget is an independent web element that can be placed commonly on the user interface of any website or software to facilitate a set of features
SSO Widget is placed in the header of all e-Services (Government Digital Services) that are connected to the JISF SSO. Using this widget users will be able to switch from one application to another. For example, users will be able to switch from Application 1 to Application 2 using this widget.
No Comments